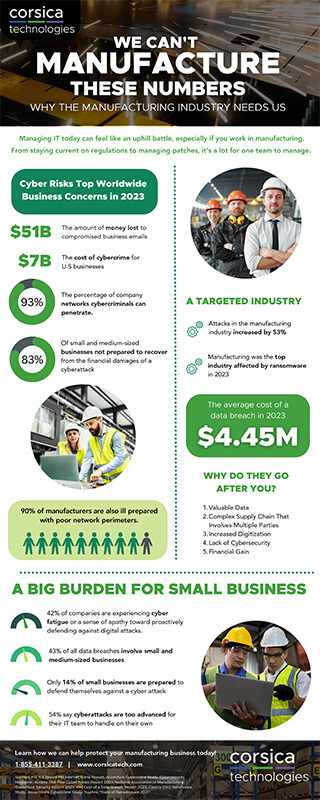
Thirty-nine percent of advanced manufacturing executives say their companies were breached in the past year, and 75% say they lacked resources with essential cybersecurity skills. Cybersecurity is essential to keeping manufacturing businesses running.
Availability is a key cybersecurity concern in manufacturing. Because downtime means you can’t manufacture your product, you could be losing money for every minute of downtime. In this article, we’ll address concerns specific to manufacturing, share best practices to protect your business, and help you solve the cybersecurity skills gap.
Industry Security and Uptime Considerations
Like other industries, some of the most serious threats to manufacturers include phishing, ransomware, and distributed denial-of-service (DDoS) attacks. These can take systems offline or make them unusable.
But in addition to these universal cybersecurity concerns, manufacturers face some specific threats. One is that some legacy production systems rely on outdated applications, making them vulnerable targets for attackers.
In smart and advanced manufacturing companies, the convergence of IT and operational systems carries risks. While IT is focused on security, operational technologies (OT) are built for availability. They may not be patched on a regular basis because that can take the tech offline.
Though manufacturers can experience attacks of opportunity, they are also at risk of targeted attacks by those who know that manufacturers are more likely to be using outdated or vulnerable applications. Whatever the motive or source of attack, these risks are why it’s so important to follow best practices.
Cybersecurity Best Practices for Manufacturers
These are some of the most important cybersecurity best practices for manufacturers to follow. By establishing good cybersecurity hygiene, you minimize the risk of downtime and loss caused by attacks.
Conduct cybersecurity risk assessments
One of the most important security practices is to regularly perform cybersecurity risk assessments. You may do this annually or more frequently as the cyber threat landscape changes. You can conduct these assessments internally or use a third party.
A cybersecurity specialist will have expertise and know about emerging threats. Even if you have skilled personnel on staff, a cybersecurity organization can provide risk management guidance.
Provide employee awareness training
Commonly, attackers will send emails to employees to try to trick them into clicking a link or providing information that will give them access to protected areas of the business. Employee training is essential because phishing and social engineering attacks are common and getting harder to recognize.
We recommend training employees as frequently and as intensely as you can without interfering with work. A cybersecurity specialist can help set up and customize training for your business.
Develop a network segmentation strategy
Keeping OT and IT environments separate minimizes the attack surface. Further segmenting these environments lets you better control networks and optimize damage control in case of a breach.
Automate monitoring
With all the servers, network infrastructure devices, SaaS applications, and IoT devices supporting a manufacturing business, it’s impossible to manually review all the log data. A security information event management (SIEM) solution automates the collection and analysis of all system logs. It also improves detection accuracy.
Establish protocols and processes
Create your security risk management protocols and processes by first determining what you want to accomplish and then documenting those goals and priorities. That way, you’ll have a guide for your technical configurations.
Reduce Downtime in Manufacturing
The cyber threat landscape is always changing. Manufacturers can better protect their businesses and overcome skills shortages by partnering with cybersecurity experts to conduct risk assessments, train employees, and establish processes and protocols.
To learn more about minimizing line downtime, talk to one of Corsica’s specialists in cybersecurity and IT for manufacturing.