Pen Testing Services 101
Your comprehensive guide to preparation, vendor
selection, fixing vulnerabilities, and more
Pen Testing Services 101
Your comprehensive guide to preparation, vendor
selection, fixing vulnerabilities, and more
Are you easy to hack?
That’s the big question. Today’s cyber threat environment is evolving faster than ever, and what worked yesterday may not protect you today.
Yet many organizations don’t even know where their weaknesses lie. They have no visibility into these issues until the unthinkable happens.
Penetration testing (pen testing) solves this problem. This is a service provided by a company that specializes in cybersecurity and ethical hacking. The goal of the exercise is simple: Try to breach a system in the same way real hackers would—and see what happens.
While the high-level benefit of pen testing services is clear, there’s a lot to know. Can you conduct this test yourself? What does the process look like? If you’re choosing a third party pen testing company, what should you look for?
We’ll answer all that and more. Let’s dive in!
Contents
1. What are penetration testing services?
Penetration testing (pen testing) is a cybersecurity exercise that reveals how easy (or difficult) it is to hack your network.
Theoretically, your team could conduct penetration testing themselves. But if they’re the ones who designed your network and continue to maintain it, they may not be the right people to test its defenses.
Penetration testing services help close this gap. These services are conducted by “ethical hackers”—cybersecurity experts who can hack just about anything but only use their powers for good. They’re “the internet’s immune system,” according to cybersecurity expert Keren Elazari.
Need a pentest? Contact us now →
As you can imagine, penetration testing services are essential in today’s threat landscape. They’re the only way to find out the true strength of your network security.
But how is pen testing different from vulnerability scanning?
Great question!
2. Pen testing vs. vulnerability scanning
If you’re familiar with vulnerability scanning, you might wonder if pen testing services are the same thing. After all, both exercises are all about network security. So what’s the difference?
Actually, pen testing and vulnerability scanning are quite distinct. Here’s what you need to know.
Vulnerability scanning is a passive exercise

Vulnerability scanning, as the name suggests, is all about finding vulnerabilities. The output of vulnerability scanning is a report of known vulnerabilities, but this exercise doesn’t involve ethical hackers actively trying to breach your systems.
Pen testing is an active exercise
A good pen test starts with a list of known vulnerabilities—but it goes much farther than that. Rather than simply reporting these potential problems, human actors try to exploit these weaknesses—both those already known, and those unknown before the start of the test.
Vulnerability scanning relies on automated detection
Modern vulnerability scanning software is incredibly sophisticated. But at the end of the day, it’s still automated. This means it’s only as good as the configurations and rules programmed into the solution. Vulnerability scanning can’t see potential ways to exploit multiple vulnerabilities together, as a human hacker can.
Pen testing relies on human intelligence and problem-solving
It’s one thing for a vulnerability to exist. It’s another thing entirely for a threat actor to exploit it.
Simply put, it takes real expertise, intent, and perseverance to chain together a series of vulnerabilities into an intelligent attack. By definition, vulnerability scanning can’t demonstrate how your network responds to a real hacking attempt. Pen testing services provide those real-world results.
3. Why choose a pen testing services company?
Theoretically, you could conduct penetration testing yourself—if you had the expertise on staff.
But most companies don’t have pen testing expertise. And even if you did, you want to think about the potential conflict of interest. If your pen testing experts are the same ones who designed your company network, do they really want to expose the weaknesses in their own work?
This is the biggest reason to choose a third party company for pen testing (rather than doing it yourself).
But it’s not the only benefit you get. Here are 7 great reasons to choose a pen testing services company.
1. You get the outside perspective you need

A good pen testing company will have ethical hackers on staff who are career experts in cybersecurity. Unlike internal resources, these ethical hackers don’t particularly care if your network passes or fails the test. In fact, they have no skin in the game other than overturning every stone—and finding every possible attack vector.
2. You get the data you need to strengthen your security posture
You can’t mitigate weaknesses if you don’t know what they are. While the results might not be what you want to hear, they’re the first step in getting stronger.
A pen testing company also gives you a powerful deliverable—a report of vulnerabilities that were exploited (and how they were exploited). This document gives you (or your cyber security managed services provider) a clear path to improve your security posture.
3. You get real-world results, not just potential entry points
As we discussed above, vulnerability scanning reveals potential entry points for a network breach.
A pen testing company gives you a report of real entry points for real breaches conducted by ethical hackers. There’s simply no other way to get that information—other than being hacked by criminals.
4. Your network team can gather significant takeaways from the findings
Even the most seasoned IT professionals need to keep learning. Operating systems, patches, and threats are always evolving.
Regular penetration testing gives your network team the real-world data they need to stay sharp. There are always takeaways from a penetration test, and your IT staff will reap the benefits in new learning.
5. You can raise awareness of cybersecurity within your company
 Everyone knows cybersecurity matters, but not everyone knows how much.
Everyone knows cybersecurity matters, but not everyone knows how much.
Knowledge of specific cybersecurity controls is also rare. Your team may have no idea just what it takes to keep your organization secure.
Sharing the results of a penetration test within your company can raise some eyebrows. While the results may be uncomfortable, they may be just what your organization needs to start thinking hard about cybersecurity.
6. You can use the results to get buy-in for better cybersecurity controls
When budgeting time comes around, every department competes for a limited number of dollars. It’s challenging for leadership to make the right decisions in allocations, and even the best-intentioned executives can miss out on crucial cybersecurity information. Ultimately, this leads to reduced cybersecurity spending—and greater exposure to a breach.
The results of a penetration test can help get the executive attention you need to address cybersecurity. This is especially true if your company has never emphasized cybersecurity before.
7. You can make intelligent decisions about cloud vs. on premises solutions
While cloud is the buzzword today, it’s important to understand that not every system should be served in the cloud. You need to analyze the long-term cost carefully—and security is an essential component in that calculation. A penetration test can help you determine if you’re using the right delivery model for a particular system.
4. Types of pen testing services
Depending on what systems your organization uses, you’ll need a specific type of pen testing services—or perhaps more than one. Here are the main types to be aware of.
A) On premises network penetration testing

This type of pen testing applies to on-premises networks and systems. Broadly speaking, there are two subtypes—external vs. internal penetration testing. While they sound similar, they’re actually quite different.
External penetration testing takes place from outside your network. Ethical hackers start with nothing but an internet connection, i.e. no access to your network at all, and see if they can get in.
External pen testing is powerful because it replicates the scenario most hackers will face if they try to attack your organization. It measures the first line of defense—can a threat actor gain access to your network? If so, how?
Internal penetration testing takes place from inside your network. Ethical hackers start with some degree of access and see how far they can penetrate further, using various exploits. An internal pen test can (and should) follow an external one, but it can also be performed on its own as required.
Internal pen testing tells you what can happen after a hacker gains access. It reveals how easy it is for a threat actor to move laterally within your network, and it often provides takeaways—such as the need to implement a Zero Trust framework.
B) Cloud system penetration testing

Cloud systems come with unique security risks. As CrowdStrike explains, factors like unmanaged attack surfaces, human error, and misconfiguration all contribute to the vulnerability of a cloud system.
Cloud pen testing helps to uncover these weaknesses. It also shows how real-world hackers can exploit them to breach the cloud system.
As with on-premises systems, cloud systems should be tested by ethical hackers who’ve been granted varying levels of access. This provides a broad spectrum of pen testing outcomes.
C) Web application penetration testing
Web applications—i.e., software solutions delivered through a web browser—come with unique cybersecurity risks. The biggest ones include:
- Injection attacks, in which a hacker exploits a bug caused by invalid data and uses it to alter the execution of a command.
- Security misconfiguration, in which a highly configurable web application has not been thoroughly set up to maximize security.
- Vulnerable and outdated components, which occur when a web application depends on any type of software (OS, database management system, APIs, and more) that is out of date or known to contain vulnerabilities.
A web application pen test attempts to breach a web application using these and other types of entry points. As always, the goal is to see what real-world hackers can do. If your organization develops and sells web applications, this type of penetration testing is essential. However, some organizations may choose to conduct pen tests against web applications that they use as well. In this case, it’s best to let your web application provider know that you plan to conduct a penetration test on your instance of the software.
D) Mobile application penetration testing
Due to their unique architecture, mobile applications come with potential vulnerabilities that should be examined through pen testing services. Dependence on third-party APIs creates a unique attack surface, while lackluster encryption can make mobile apps especially easy to hack.
Between these factors and others like weak authentication policies and unpatched vulnerabilities, mobile apps need regular pen testing to keep them secure.
5. Should you schedule pen testing services during off hours?
This is a great question.
A penetration test is a real hacking exercise. It involves scanning systems for vulnerabilities, then attempting to exploit those vulnerabilities in real time. This makes even the most experienced IT admin a little nervous!
Broadly speaking, these concerns fall into two categories.
- Concerns about server load. Will the vulnerability scanning software, and the hackers themselves, place a disruptive load on a server that’s processing critical information or traffic during business hours? If so, how will any downtime impact operations and revenue?
- Concerns about data loss. Will the ethical hackers accidentally delete essential data in the course of an exploit?
Here’s the good news. Ethical hackers are… ethical!
Your hackers will work closely with you to ensure they provide a valuable test without harming the business. Generally speaking, vulnerability scanning software doesn’t produce a big enough load to take down a server. If that load is big enough to take down a server, then the device had issues to begin with, and your ethical hackers will include this information in their report.
Likewise, your pen testing team isn’t going to conduct DDoS (dedicated denial of service) attacks or hold essential data for ransom. Their goal is to infiltrate a system—not actually take it down.
This is important because off-hours pen tests may cost more than those conducted during business hours.
It’s rare that an organization truly needs off-hours pen testing. That said, talk to your pen testing company if you’re concerned about conducting the operation during business hours. The right company will advise on the best way to approach pen testing in your scenario.
6. What to look for in a pen testing company
Many cybersecurity companies offer pen testing services, but it pays to be selective when you look for a partner. The quality of a pen test is dependent on the expertise of the ethical hackers who conduct the test. First and foremost, you want to understand the background of the hackers who will conduct your test.
Beyond that, you should also consider what happens after the exercise. A good pen testing company will provide a detailed report of what happened, with recommendations for mitigating vulnerabilities. You’ll want to think about who’s going to implement those changes.
Here’s everything you should look for in a reputable pen testing company. Consider bringing in your IT staff (or your MSP) to help evaluate a pen testing company.
Career experts in ethical hacking

It takes a certain type of person to succeed as an ethical hacker. The University of Denver puts it this way: “Those with a curious mind, a taste for coding, and a tenacious personality may want to consider [a career in] ethical hacking.”
While these qualities are essential, they’re just the foundation for a great ethical hacker. When your organization conducts a pen test, you want ethical hackers with deep experience. Consider asking to see the resumes or LinkedIn profiles of the hackers who work with your pen testing company. The right partner should offer transparency here, allowing you to judge the experience and expertise of their team members.
Experience with the systems you need to test
Depending on what type of system you’re having tested, you may need a partner with specialized experience breaching that type of system. Thoroughness is important here, since pen test services are only as good as the hackers are thorough. You want experts who really know how to work with the systems in question. This is the best way to ensure your ethical hackers overturn every stone.
Consulting expertise to define your path forward
It’s one thing to offer pen testing services and a report detailing the outcome of the exercise. But what do you do with that information?
The right pen test company should also provide clear guidance on your path forward. For every vulnerability and attack vector uncovered, your partner should give you a coherent plan for mitigating risk.
Full-service MSP/MSSP (not just a pen testing company)
Most organizations lack the cybersecurity resources to mitigate vulnerabilities uncovered by pen test services. Unless you’re a global enterprise with an internal cybersecurity team, you’ll need a trusted partner to implement the increased cybersecurity controls that your pen testing company recommends.
You could look for another company to implement these controls—but you’ll get more bang for your buck if your pen testing company is also a full-service IT and cybersecurity provider, i.e. a combined MSP/MSSP. Working with a company like this gives you synergy across teams and systems that’s difficult to achieve when you work with multiple vendors.
7. Penetration testing steps
Different pen testing companies will use different methodologies. Your provider can explain the exact process that they’ll use.
That said, all methodologies ultimately work toward the same thing. Generally speaking, here are the steps your provider will take as they execute your penetration test.
1. Intelligence gathering

Before a hacker tries to breach your systems, they’ll take time to gather as much publicly-available information as they can. This means analyzing all systems that are connected to the internet and getting a sense of the potential attack surface.
Your ethical hacking team will do the same thing. Just like unethical hackers would, they’ll analyze the entire publicly-accessible attack surface of your network. This ensures that your penetration testing service is thorough, leaving no stone unturned.
2. Network & application reconnaissance
Now it’s time to take an inventory of your assets. This means sweeping for live hosts and services running within your network’s range. Any such host or service may provide an entry point, so it’s essential to be thorough. Your pen testing company needs to try everything when they attempt to breach your systems.
3. Vulnerability discovery & analysis
Once your pen testing company has established a list of all live hosts and services running in your network, it’s time to find any vulnerabilities that may exist. The pen testing team will use interactive procedures to audit your endpoints, processes, technology, and network for vulnerabilities.
4. Ethical hacking exercises
Now the fun begins!
The ethical hackers will use all the information they’ve gathered to hack into your systems (if they can). This phase will look different depending on what vulnerabilities and potential attack vectors were discovered. The team will log everything to make sure you get a comprehensive penetration test—and a highly detailed report.
5. Executive summary & formal presentation

The results of pen testing services aren’t just for the IT team. All stakeholders need to understand the findings of a penetration test.
This is why the best pen testing companies present a formal executive summary in plain language. Every stakeholder deserves a clear explanation that they can understand. Likewise, the best providers invite discussion when they present the findings, so stakeholders can ask questions and leave with answers.
6. Technical report & targeted action plan
The executive summary is essential for cross-functional understanding of the findings. But ultimately, pen testing services reveal technical gaps in cybersecurity. Therefore, the best pen testing companies provide both a technical report and a targeted action plan to maximize the value of the exercise.
The key here is the targeted action plan, which provides a roadmap for mitigating any vulnerabilities uncovered. Without execution of this roadmap, your existing vulnerabilities will remain, and new ones will likely arise.
If your company has the staff resources, you may choose to implement the remediation plan yourself. If you don’t have those resources on staff, your pen testing company may be able to implement them—or recommend an expert partner to assist.
8. How to prepare for your pen test
Setting up a pen test isn’t as simple as making a phone call and picking a date. To get the most out of the process, you need to put some time and effort into the preparations.
Here’s what that looks like.
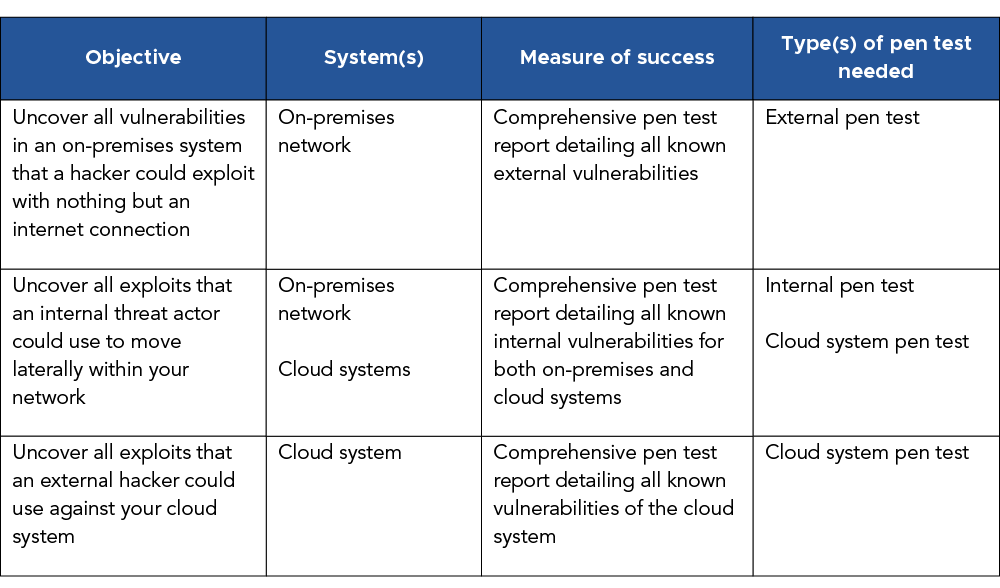
A) Define your pen testing objective, system scope, and measure of success
Why are you conducting a pen test?
While the answer to this question may seem obvious, you want to get specific.
Are you concerned about external vulnerabilities exposed on the internet?
Are you concerned about internal vulnerabilities, and you want to see how easy it is for an inside threat actor to move laterally?
Are you concerned about the security of a cloud system?
Whatever the situation, you should define your specific objectives, as well as the systems that you’ll test. Only then can you define your measure of success.
Here are some objectives we commonly see, plus the corresponding systems, measures of success, and types of pen test needed.
B) Let your IT team know you’re planning a pen test (and include them)
Whether you have an internal IT team, a managed network services provider, or a combination of the two, you’ll want to bring your IT experts into the process. Your admins need to know that a pen test is going to happen.
This will prepare them for any alarming notifications, but they can actually play a larger strategic role, too. With their expertise, they’re the ideal resources to consult as you evaluate pen testing companies (next step).
C) Evaluate pen testing companies and select one
Now it’s time to find a qualified pen testing company.
While there are many organizations that offer pen testing services, you’ll want to do your research and ask tough questions. Your IT team may be able to help vet potential partners.
For details, see above, What to look for in a pen testing company.
D) Schedule your pen testing services
Once you’ve chosen a company, it’s time to get that penetration test on the calendar.
But when should you schedule your test? Should it occur during off-hours to minimize the impact to essential systems? Or is that not worth the extra expense?
See above, Should you run pen testing during business hours?
E) Prepare your environment(s)

A pen test will poke and prod the environment in question.
Any time you’re doing that, it’s a good idea to make a backup of any essential data.
You might also consider conducting the pen test on an exact copy of the production environment. While a pen test shouldn’t disrupt the system in question, using a mirrored environment will minimize any potential impact to the business. This practice can also help address the concerns of stakeholders who are worried about how pen testing services may affect critical systems and data.
Depending on the type of pen test, the ethical hackers may also need access to certain systems. This is especially true if you’re doing an internal penetration test. In that case, you’ll want to create accounts for the ethical hackers, or else share existing credentials with them in a secure manner.
F) Whitelist the ethical hackers’ IP addresses
This step is easy to overlook.
If ethical hackers are going to access your systems, you’ll need to ensure their IP addresses are whitelisted. Do this ahead of time, and you’ll ensure the operation goes smoothly on testing day.
G) Establish communication protocols for the testing process
Unlike real hackers, ethical hackers make themselves available for communication during the hacking exercise. Typically, your pen testing company will provide a point of contact who works with the hacking team. Your organization should also designate a point of contact and establish expectations and communication protocols before the event starts. This way, that everything goes according to plan when the exercise starts.
H) Remind your IT team that the test is starting
If you brought your IT team into the vendor evaluation process, it’s worth keeping them updated as the test draws closer.
If you haven’t brought your IT team in yet, now is the time. You’ll want to let them know the date and time when the test begins, the systems being tested, and how long the test should run.
There’s one exception to this rule. Some companies may intentionally conduct a pen test without telling internal resources about it. This allows your organization to test its response to an intrusion—although this needs to be strategized carefully, with structure in place and a designated point at which to inform your team on what’s going on. The right pen testing company can help you construct this type of exercise.
I) Remain on standby during the test
It’s a good idea to keep your point of contact available during the pen test. If the hacking team encounters any unplanned issues or has questions, you want to address them quickly to get the most value out of the test.
9. Threats typically uncovered by penetration testing services
Some penetration tests uncover only a few threats. Others find many vulnerabilities. At a high level, here are the most common issues uncovered by pen testing services. This list isn’t exhaustive, but it does show the wide range of vulnerabilities that can exist on a network without anyone realizing it.
Misconfigured firewalls

Having a firewall in place isn’t enough. You also need to configure that firewall appropriately. The requirements may vary depending on your business or applicable regulation. In some cases, the default configuration of a firewall may be too permissive for your scenario.
Weak or obsolete encryption
An older system may still be running outdated encryption protocols. These protocols may pose a risk because they are less complex than modern protocols—or because they’ve actually been broken in documented attacks.
Password vulnerabilities
Older systems may have less stringent password requirements that leave them vulnerable to attack. In some cases, a system may have a default password in place that was never changed. Penetration testing services frequently uncover these types of password issues.
Authorization vulnerabilities
Improper control of user privileges can lead to more user accounts having more sensitive access than they need. This can happen when the default privileges for new accounts are too comprehensive, and there is no program in place to limit access to the principle of least privilege. Lack of thoughtful controls here can lead to vulnerabilities due to user accounts having greater default access than they should.
Deprecated operating systems

The moment an operating system is released, its days are numbered. Hackers start exploring it for vulnerabilities, hardware keeps evolving, and the time will come for the OS to be deprecated and replaced with the newest version. Unfortunately, organizations with limited IT resources may struggle to execute operating system updates in a timely fashion. This can lead to vulnerabilities once an OS is no longer supported by the vendor.
Unpatched operating systems
Even while an operating system is still supported, it can’t stay static. Vulnerabilities are discovered all the time, and the OS vendor releases patches that must be applied to keep the system secure. Unpatched operating systems are one of the easiest ways for threat actors to execute a breach.
Unpatched applications
Just like operating systems, applications often require patches to mitigate vulnerabilities. Unpatched applications give hackers an easy entry point to execute an attack.
Injection attacks
An injection attack takes advantage of a bug in processing to “inject” malicious code into the data exchanged by two systems. It’s especially dangerous, as it’s often seen in attacks against databases and other essential systems.
Cross-site scripting attacks
This is a specific type of injection attack that inserts malicious scripts into data exchanged by trusted websites. Without a penetration test, this type of vulnerability is difficult to detect until the unthinkable happens.
Lack of monitoring and logging
At the end of the day, effective cybersecurity requires real human experts taking ownership of all things security-related. 24/7/365 monitoring and logging of traffic are essential components of an effective cybersecurity practice. Penetration testing services can reveal a lack of monitoring and logging, empowering you to address these issues before something happens.
10. Next steps after penetration testing
The results of a penetration test can be uncomfortable. The goal was to uncover issues, and every system has them—even the best-designed.
The key here is not to focus on the negative, but to look at the path forward. The findings of a penetration test give an organization concrete steps to creating a more secure environment.
Yet most midmarket companies don’t have the resources on staff to deal with the test results.
If that’s the case, you should look for an MSSP (managed cybersecurity services provider) who can implement the controls you need. Ideally, this partner should act as an extension of your IT team, working collaboratively and bringing their expertise to bear on your environment.
Corsica Technologies has solved this problem for 1,000+ clients. We cover cybersecurity services from top to bottom, including pen testing services, 24/7/365 monitoring, incident remediation, strategic planning, and more. You get access to an entire team of cyber professionals—without breaking the bank.


