If you’ve ever received an “urgent” email that didn’t quite seem legitimate, then you’ve experienced phishing.
Unfortunately, phishing emails represent a significant threat for organizations that are unprepared—particularly those that don’t have a cyber security managed services provider. Human beings are the weakest link in any security program, and that’s especially true when it comes to phishing emails.
But how do you test your employees’ readiness to resist phishing attacks?
And what do you do with the results of those tests?
Here’s everything you need to know.
Why give your employees phishing tests?
There’s no silver bullet that can prevent phishing emails from reaching your employees’ inboxes. Even the most intelligent email filters can miss the most intelligent phishing attacks—and threat actors are always devising more sophisticated strategies.
In other words, phishing training for employees is your #1 defense against phishing attacks.
Specifically, phishing training offers numerous benefits that you can’t get any other way:
- Your employees get exposed to phishing tactics in a no-risk scenario
- You learn which employees are most susceptible to phishing attacks
- You get a path forward for training all employees, regardless of their current knowledge, to be world-class phishing detectors
- You give your employees the experience they need to feel confident as they face increasingly sophisticated phishing attacks in their inboxes

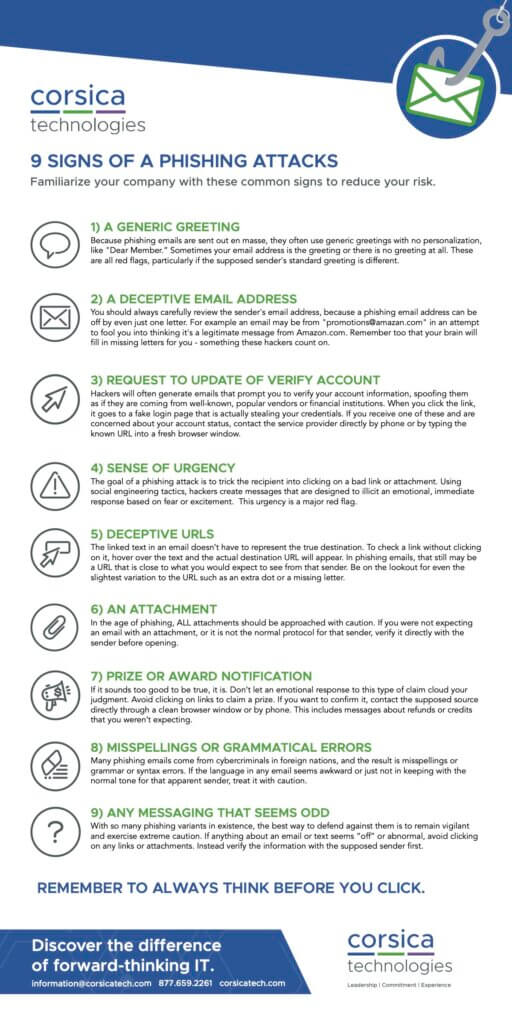
7 types of phishing attacks that your employees should recognize
Phishing attacks have grown incredibly sophisticated since they first began in the 1990s. Today, threat actors use a wide range of strategies to trick well-meaning users. The list below isn’t exhaustive—but here some common types on which you should train your employees.
1. Classic phishing
This is the old standby of the phishing world. An attacker sends an urgent email that appears to be from a reputable source—often a well-known company like PayPal or Amazon. Since anyone can download a company logo from the internet and use a sender name like “PayPal Customer Service,” there’s nothing to prevent these types of emails from being sent.
As with so many phishing examples, urgency is the key here. The email may warn the user that their account has been compromised, or that they need to make an extra payment for shipping to get a product they ordered. The CTA (call to action) is often quite bold, telling the user to click a large, colorful button (or download an attachment) to fix the situation.
In the case of the button, hovering over it rather than clicking should display the linked URL. If this URL looks phishy… it is! In fact, this is one of the easiest ways to detect any type of phishing email that relies on the user clicking a link.
Malicious attachments can be more difficult to spot, as there is no “hover to discover” option. The good news is that phishing training can give your employees the tools they need to respond when they get a suspicious attachment.
2. Spear phishing
The classic phishing email takes a wide aim at numerous individuals. While it may include a personalization token that displays the employee’s name, the message itself and the malicious link (or attachment) are not personalized. Every victim of the attack gets the same message and link.
Spear phishing is personalized.
In this type of attack, the threat actor targets a specific individual after gathering data about them. Name, contact information, title, and other professional details all contribute to a convincing spear phishing attack. The threat actor sends a highly personalized message with details that come from the victim’s real life. This makes spear phishing even more dangerous than a classic phishing attack.
Ultimately, spear phishing leads the victim to the same destination as classic phishing—a malicious link or attachment. The only difference here is the strategy for gaining the victim’s attention and manipulating them.
3. Executive impersonation
Valuable employees care greatly what leadership thinks of them. If a leader comes to an employee with an urgent task, the employee’s first instinct is to jump on it.
This is the exact psychology that attackers seek to manipulate.
An executive impersonation attack may spoof a company email address or cell phone number, appearing to come from the CEO (or another executive).
From this point, the strategy can take different forms. Some attacks may target individuals in finance or accounting who have the authority to initiate wire transfers. Other attacks may target any type of employee with a message about an urgent task, asking the victim to call the executive on their “personal cell phone.” Naturally, the number is fraudulent—but it’s a smart move, as lower-level employees may not have the personal cell numbers of C-level executives.
4. Whaling
Executive impersonation is all about faking the executive’s identity and targeting another employee.
Whaling flips this model around. The target is the senior executive—a person who has widespread access to sensitive networks, systems, and data.
In reality, whaling is a form of highly-targeted spear phishing. Executives may have prominent status within their industry, with lots of information about them available online. This makes it easy for a dedicated phisher to craft a message that tricks even the most careful executive.
5. Clone phishing
Clone phishing is another form of specialized spear phishing. The attacker gains access to a legitimate email message in the victim’s inbox, then crafts a new email that appears to come from the same person, continuing the conversation. The email may include language like “resending this,” plus a malicious link or attachment.
Clone phishing can be especially tough to spot, since it comes with so many apparent trust signals.
6. Vishing
“Voice phishing,” or vishing, is the practice of phishing over a phone call. Since vishing refers only to the type of technology used, a vishing attack can take any form we’ve already covered.
In the business world, an attacker may pretend to represent a legitimate company that has a relationship with the targeted organization. This could mean impersonating a customer, supplier, or other type of partner. Because employees care about the relationships that matter to their company, they’re more likely to fall for the manufactured urgency and comply with the caller’s request.
7. Smishing
“SMS phishing,” or smishing, is the practice of phishing via text message. Like vishing, smishing refers only to the technology by which the attack is delivered. Specific strategies like spear phishing, executive impersonation, and whaling can all be delivered via SMS—in which case they would also be smishing attacks.
Smishing is powerful because the only information the victim can see is the attacker’s phone number. There’s no “hover to discover” possibility like there is with email-based phishing schemes that depend on a malicious link. This makes smishing especially dangerous in scenarios where the user wouldn’t know the sender’s phone number if the message was legitimate—for example, in executive impersonation.

How do you actually test your employees for phishing awareness?
While you could set up a special domain and email address to do this yourself, that’s usually more trouble than it’s worth. A good phish testing solution takes care of the technical side. It should also provide the ability to send realistic-looking phishing emails with a minimum of effort.
In addition to the technical side, you need expert human attention designing and running your tests, then analyzing the results. Many organizations lack the staffing capacity to do this in-house.
For these reasons, it’s best to use a third-party testing solution managed by an expert partner. Here at Corsica Technologies, we offer access to world-class phish testing provided by KnowBe4 as part of our Security Awareness Training. The solution gives us access to 20,000+ templates for phishing emails, which means we can drill down and create emails that look legitimate in the context of your industry and partner relationships. The software also allows us to see test results, which we share with you as we collaborate on training your employees.
The process of employee phish testing
Whether you do the testing yourself, or outsource it, here’s what the process looks like.
- Establish a baseline. You’ll send your first phishing test without letting your employees know it’s coming. The results here will give you a clear baseline for each employee on your team. You can see who’s advanced, who’s average, and who needs the most help.
- Implement phishing training. Even high-performing phish detectors should get comprehensive training on phishing, particularly if your organization has never done this before. Yesterday’s phishing training may not cover today’s threats, so it’s best to start everyone at square one.
- Test again. This time, you may (or may not) choose to let your employees know that you’re conducting the test. You’ll want to note any improvements as well as any movement in the wrong direction.
- Establish a regular cadence of training and testing. Unfortunately, phishing attacks continue to evolve. It’s essential to stay ahead of the curve with regular testing and phishing training.
As you can see, testing your employees is a fairly significant undertaking. Organizations that are large enough to have a dedicated cybersecurity team may be able to do this in-house. However, companies that don’t have those in-house resources typically struggle to manage phish testing on their own. These organizations see the greatest benefit when they outsource phish testing as part of a larger security awareness training package.

What to look for in phish testing services
Phish testing partners aren’t created equal. You’ll want to find a provider who knows phish testing inside and out—so they can adapt it to your unique industry and context.
Here’s what you should look for.
Comprehensive security awareness training
Phish testing is only one component in an effective security awareness program. Your employees need to get the full picture—not just phish detection training.
The right provider should offer customizable training packages that are tailored to your organization. This ensures that your employees get the comprehensive training they need.
Tons of phishing email templates
Phishing is always evolving—and so your phish testing should evolve, too. Yesterday’s phish testing template is more recognizable every time it’s sent. You need the ability to iterate and try new messages.
You also need messages that are customized to fit your industry and your organization’s context. The more realistic a phishing test is, the more effective it is.
For both of these reasons, you should seek out phish testing services that offer tons of email templates. Here at Corsica Technologies, our phish testing comes with 20,000+ templates. You can rest assured that your phish testing emails will look realistic in the context of your business—and they can keep evolving.
Centralized software for sending tests and seeing results
Whether you’re assisting with the phish testing program, or entrusting it completely to a cybersecurity partner, you’ll need centralized software that controls your tests. This allows you (or your cybersecurity partner) to send tests and see results within a single user interface.
Browser protection + email protection
While it’s essential to train employees on phishing emails, you have to be realistic about the limitations of training. On their worst day, under significant stress, even the best-trained employee can make a mistake.
That’s why you should implement solutions for browser protection and email protection. Hint: Here at Corsica Technologies, we offer Corsica Browser Protection and Corsica Email Protection. Together, these software solutions help guard your employees from even seeing malicious emails or reaching malicious websites.
Can assist with cybersecurity policy development
Once you start training employees on examples of phishing emails, you’ll realize that you have to define what you expect of employees in this area. Yet cybersecurity policy goes far beyond phishing training, safe email usage, and safe internet browsing. You’ll need to develop comprehensive policies that cover all aspects of cybersecurity at your organization—or update these policies if you already have them.
This task can be overwhelming. The right partner will offer templates and an expert perspective to help you get the up-to-date policies you need.
The takeaway: Test employees with phishing emails… but don’t stop there
Phish testing is an essential component in training employees on cybersecurity, but it isn’t enough. The right training program will cover cybersecurity from top to bottom, equipping your team to defend your organization in every scenario.
If you need help training your employees, reach out today. Our specialists can devise customized phishing training packages that fit the unique needs of your organization.

Want to learn more about phish testing for employees?
Reach out to schedule a consultation with our security specialists.






