The Rise of Strategic Outsourcing in Cybersecurity and IT

Midmarket companies face many challenges in today’s fast-changing technology environment. From cybersecurity to strategic IT roadmaps, AI to data integration, the challenges are numerous. How do the best-performing companies respond? What do they outsource, and what do they cover in-house? This in-depth whitepaper examines the results of a comprehensive survey conducted by IHL Group, a […]
Whitepaper: Incident Response & Containment

What processes and roles should you establish BEFORE an incident occurs? What does the incident response process look like? Whether you’re handling this yourself or looking for an MSSP (managed security services provider), our in-depth whitepaper gives you everything you need to know about responding to cybersecurity threats–and containing them. We cover: Download the whitepaper […]
Cyber Security Services 101

You know you need cyber security managed services. But where do you start? How do you compare providers, fill gaps, and make sure you don’t spend more than you need to? Download our FREE Guide to Cyber Security Managed Services to start the process of choosing your ideal provider. The guide covers:
Reduce Manufacturing Downtime with Cybersecurity

39% percent of advanced manufacturing executives say their companies were breached in the past year, and 75% say they lacked resources with essential cybersecurity skills. Cybersecurity is essential to keeping manufacturing businesses running. But where should manufacturers start when improving their security posture? Our whitepaper gives you everything you need to know. We cover: Ready […]
Generative AI Policy Template
Whether you’re comparing Microsoft Copilot and ChatGPT, developing general policy, or protecting cybersecurity, there are many decisions to be made in AI policy. But where do you start? How do you ensure your generative AI policy covers all the bases? Our FREE template gives you the structure and language to get started. We cover: Note: […]
CJIS Compliance Checklist

CJIS databases provide one centralized source of criminal justice information for agencies around the country. And if you’re going to work with CJIS data, you need to meet certain cybersecurity requirements. But where does your organization stand? What do you need to do to achieve compliance? Our CJIS Compliance Checklist gives you everything you need. […]
Cybersecurity RFP Template
Looking for the right MSSP (managed security services provider)? Unfortunately, not all MSSPs are created equal. Some specialize in certain cybersecurity controls while outsourcing other controls to a third party. Some only handle cybersecurity. They don’t cover the related IT managed services. If you’re going to choose the right MSSP, you need to perform a […]
Microsoft Copilot vs. ChatGPT Side By Side
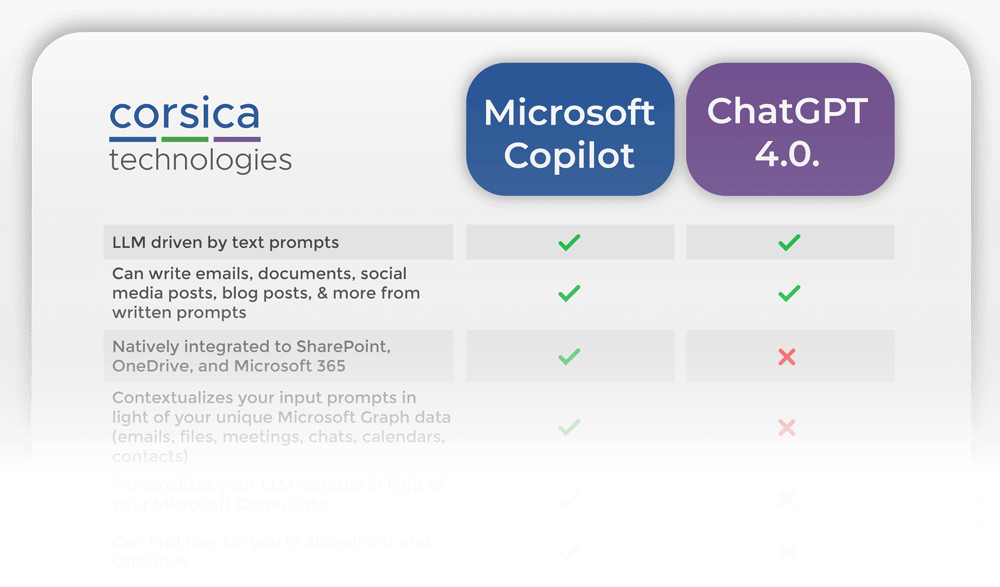
Microsoft Copilot and ChatGPT 4.0 appear similar. After all, they’re both LLMs (large language models). But that’s where the similarity ends. ChatGPT has no access to your internal Microsoft data. Copilot is natively integrated to Microsoft365, SharePoint, OneDrive, and more. Then there’s the cybersecurity question. ChatGPT is notoriously insecure from the perspective of cybersecurity. Get […]
Get Proactive: How to Build a Cybersecurity Program

A 600% increase in cybercrime during COVID-19. A 31% increase in security attacks between 2020 and 2021. As a business owner or someone entrusted with protecting your organization’s technology resources and data, you’re already painfully aware of the persistent need to defend against cyberattacks. And you’re not alone. This guide will provide you with the framework you need to build […]
How the Right IT and Cybersecurity Strategy Can Grow Your Business

Discover how the right IT and cybersecurity strategy can take your can take your company’s revenue to the next level. Within many organizations, IT and cybersecurity budgets are still considered expendable – but with the right strategy, you can take your company’s revenue growth to the next level. This guide covers:
The Difference Between an MSP and MSSP – And Which Approach is Best

When seeking a partner for your IT and security services, there are two types of providers for companies to consider: a managed services provider (MSP) or a managed security services provider (MSSP). Rapid transformations in both cyber threats and available technology have ignited a new era of business — one where your IT architecture and […]
The Decision-Maker’s Guide to Combating Cyber Threats

How to advance your IT strategy to meet the demands of an ever-evolving cyber environment. Rapid transformations in both cyber threats and available technology have ignited a new era of business — one where your IT architecture and cybersecurity strategy matters more than ever. What this guide covers:


