Recently, I was asked, “Does security monitoring make you more secure?” Aside from the obvious qualitative benefits, this question immediately prompted my curiosity to see exactly how much risk is reduced. As a provider of security monitoring services, we are in a unique position to provide quantifiable results to this question using data spanning a number of clients.
Obvious Qualitative Benefits
I would be remiss if I didn’t at least address the qualitative benefits of security monitoring. While there are several, key benefits include:
- When your employees know you monitor system activity, they are more likely to comply with your Acceptable Use Policy.
- When incidents occur, you realize there is a problem sooner rather than later, minimizing the cost to remediate and any associated impacts to your organization.
- Through the baselining process, you will often find configuration problems and other vulnerabilities that have not yet been exploited allowing you the opportunity to fix problems before things get worse.
- During deployment, you may find you currently have one or more active incidents. Correcting these allows you to start monitoring from a known secure point in time.
Not All Security Is Secure
I would be equally remiss if I did not address the proverbial elephant in the room regarding cybersecurity monitoring solutions. NOT ALL SOLUTIONS ARE CREATED ALIKE. Some solutions are simply tossed into an environment without regard to the client architecture or an understanding of the client’s actual business risks.
When I examine these solutions, I immediately think of this image:

Technically speaking, this meets the definition of a security solution and is installed correctly, but without taking a step back, looking at the surrounding architecture, and understanding the intent of the solution, this “security” solution is completely meaningless. Even worse, you wasted money on a false sense of security. Another scenario that I often see is organizations that entrust their security to low-cost security providers who claim to be as good as everyone else at a fraction of the price. With most services, the cost of delivering the services is comprised of both hard costs (the tools) and soft costs (the labor). Since the hard costs are relatively equal and are the smallest component of the price, the only way to undercut the price is to reduce the amount of labor you perform as part of that agreement. In security monitoring, the way you reduce the amount of labor is by establishing a high baseline to limit the number of alerts you receive. Unfortunately, this also means more threats go unnoticed.
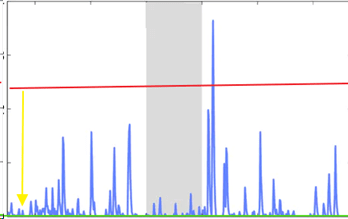
Less Alerts = Less Labor = Less Security
The graph above depicts the alert volume for a given organization. The red line represents the baseline established by a low-cost security provider. In this case, the provider alerted you to one issue throughout the month. The yellow line represents the inherent risk in your solution. Any threats which do not exceed the baseline will most likely go unnoticed, again causing a false sense of security. The green line represents a truer baseline, and all significant deviations above the baseline should be examined by a security professional. This analysis takes time, costs money, and if you are dealing with the right company, yields a much better understanding of your network, organization, and security threats.
About the Data
For my research, I examined each of our DataDefend™ clients and excluded all that did not have at least 9 months of data (3 months of baselining followed by 6 months of alerting). Taking these clients, I exported the data into Excel, created a pivot table, and then used a linear trend line of the data over the last 6 months. Taking the average starting value (month 4) and the average ending value (month 9), I calculated the Reduction of Risk (ROR). Reduction of Risk (ROR) is the term used in risk management techniques to refer to the precautionary measures to reduce the likelihood of a loss or to reduce the severity of a possible loss.
The Results
The results of my study showed all clients experienced a reduction of risk. The ROR ranged between 9.38% to 88.06%, with an average of 30.86%. Given the wide variety of ROR, I reviewed each of the clients to ascertain what caused the variations. While a much more in-depth report is in order, the clients fall into one of three categories:
Category 1 (20% or less ROR): These clients had a strong governance practice in place prior to the start of the agreement. These clients see a much smaller number of alerts because they have less anomalous traffic and fewer holes in their network defenses. These clients typically see a reduction of risk in the 20% or less categories. Category 2 (40% or more ROR): These clients had very little in the way of IT governance, accompanied with a disproportionate number of alerts, and in some cases, active threats at the time the agreement was executed. The common thread among the clients that experienced the highest reduction of risk was that it addressed the issues our SOC found on their network. These issues included:
- Insecure configuration of devices and systems
- Insecure processes, including Shadow IT (technology initiatives outside the knowledge of the IT department, or executive team)
- Poor or non-existent controls over user behavior
- Poor or non-existent controls over system software
- Poor or non-existent controls over system hardware
Category 3 (20% to 40% ROR): While there were a few clients in this category with a higher degree of IT governance and subsequently, less anomalous traffic, this group primarily describes those that were slow to adopt recommendations found through monitoring.
We can help
Every organization, regardless of size or maturity, experiences both qualitative and quantitative benefits from security monitoring. Your benefits are directly proportional to your willingness to address the problems found through monitoring. If your organization is considering security monitoring, we would love the opportunity to earn your business.






